AWS already supports the use of encrypted Amazon Elastic Block Store (EBS) volumes and snapshots, with keys stored in and managed by AWS Key Management Service (KMS). It also supports copying of EBS snapshots with other AWS accounts so that they can be used to create new volumes. Today we are joining these features to give you the ability to copy encrypted EBS snapshots between accounts, with the flexibility to move between AWS regions as you do so.
This announcement builds on three important AWS best practices:
- Take regular backups of your EBS volumes.
- Use multiple AWS accounts, one per environment (dev, test, staging, and prod).
- Encrypt stored data (data at rest), including backups.
Encrypted EBS Volumes & Snapshots
As a review, you can create an encryption key using the IAM Console:
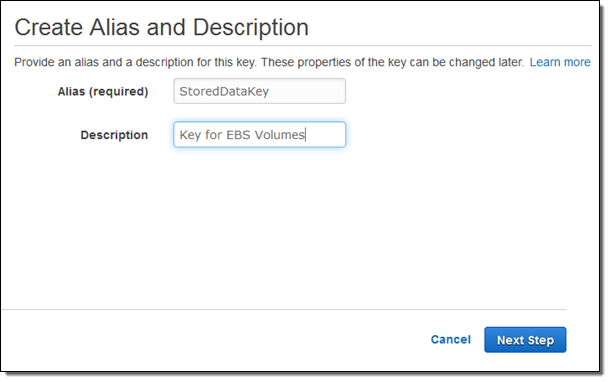
And you can create an encrypted EBS volume by specifying an encryption key (you must use a custom key if you want to copy a snapshot to another account):
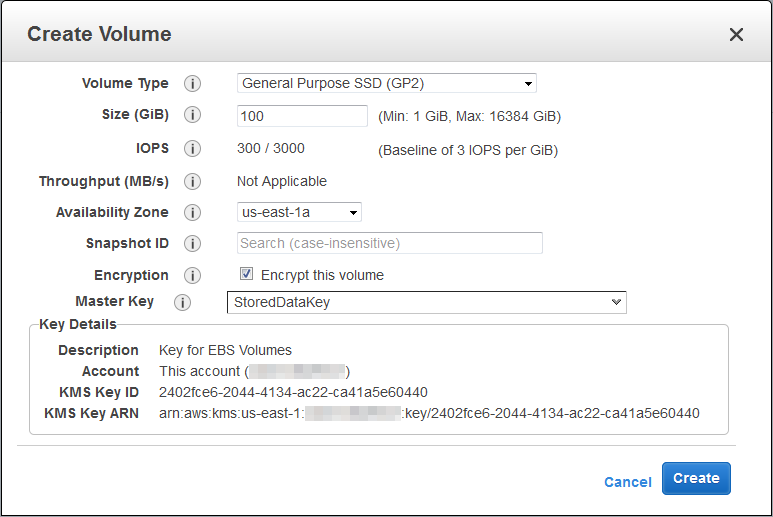
Then you can create an encrypted snapshot from the volume:
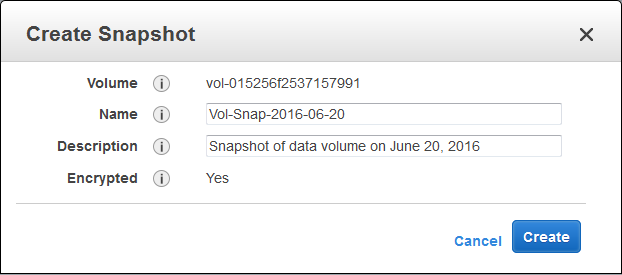
As you can see, I have already enabled the longer volume and snapshot IDs for my AWS account (read They're Here – Longer EBS and Storage Gateway Resource IDs Now Available for more information).
Cross-Account Copying
None of what I have shown you so far is new. Let's move on to the new part! To create a copy of the encrypted EBS snapshot in another account you need to complete four simple steps:
- Share the custom key associated with the snapshot with the target account.
- Share the encrypted EBS snapshot with the target account.
- In the context of the target account, locate the shared snapshot and make a copy of it.
- Use the newly created copy to create a new volume.
You will need the target account number in order to perform the first two steps. Here's how you share the custom key with the target account from within the IAM Console:
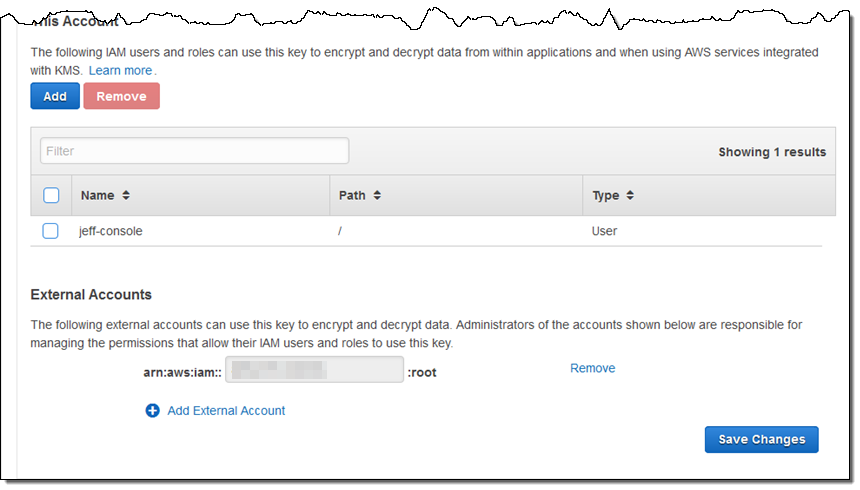
Then you share the encrypted EBS snapshot. Select it and click on Modify Permissions:
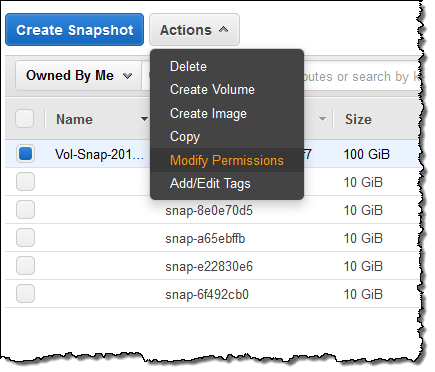
Enter the target account number again and click on Save:
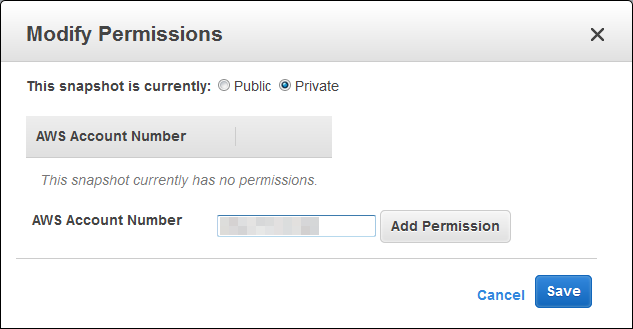
Note that you cannot share the encrypted snapshots publicly.
Before going any further I should say a bit about permissions! Here's what you need to know in order to set up your policies and/or roles:
Source Account – The IAM user or role in the source account needs to be able to call the ModifySnapshotAttribute function and to perform the DescribeKey and ReEncypt operations on the key associated with the original snapshot.
Target Account – The IAM user or role in the target account needs to be able perform the DescribeKey, CreateGrant, and Decrypt operations on the key associated with the original snapshot. The user or role must also be able to perform the CreateGrant, Encrypt, Decrypt, DescribeKey, and GenerateDataKeyWithoutPlaintext operations on the key associated with the call to CopySnapshot.
With that out of the way, let's copy the snapshot…
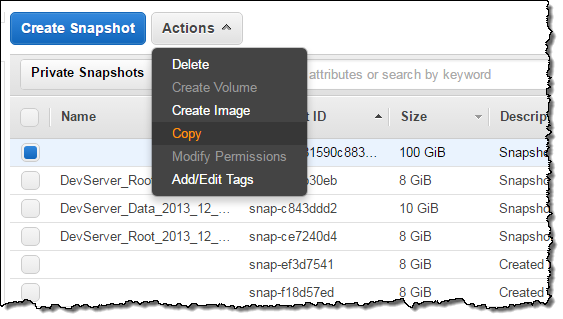
Switch to the target account, visit the Snapshots tab, and click on Private Snapshots. Locate the shared snapshot via its Snapshot ID (the name is stored as a tag and is not copied), select it, and choose the Copy action:
Select an encryption key for the copy of the snapshot and create the copy (here I am copying my snapshot to the Asia Pacific (Tokyo) Region):
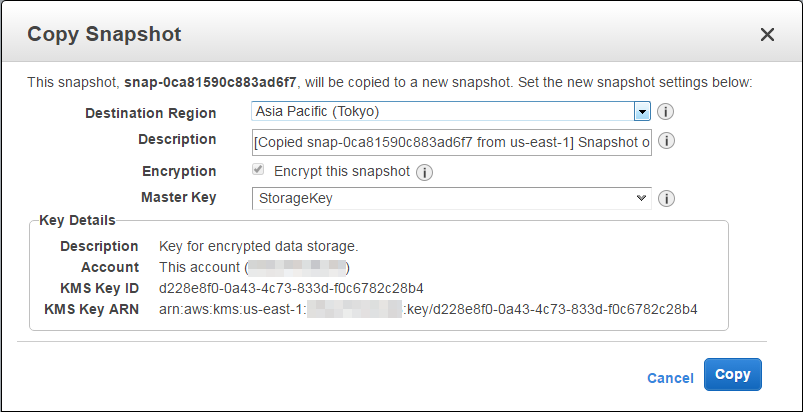
Using a new key for the copy provides an additional level of isolation between the two accounts. As part of the copy operation, the data will be re-encrypted using the new key.
Available Now
This feature is available in all AWS Regions where AWS Key Management Service (KMS) is available. It is designed for use with data & root volumes and works with all volume types, but cannot be used to share encrypted AMIs at this time. You can use the snapshot to create an encrypted boot volume by copying the snapshot and then registering it as a new image.
Jeff;
I found this blog very informative and provide valuable details on EBS snapshot. Thanks for sharing helpful post
ReplyDelete